Migrate Legacy Entra Authentication Methods
Retirement of legacy authentication methods is planned to take place soon. On April 25, 2025, Microsoft announced that legacy MFA and SSPR methods will be deprecated on September 30, 2025. After that date these policies will no longer manage authentication methods. This is why these policies need to be migrated as soon as possible. I will go over the differences between the legacy and modern authentication methods and actions to take in order to complete the migration in this article.
Important: You must migrate the legacy authentication methods before the September 30, 2025 to avoid any service interruptions
Modern vs Legacy Authentication Methods Comparison
The table below lists all of the available authentication method types in the first column. The second column lists the supported modern Authentication Strengths, which is the most up-to-date way to configure MFA. The third column lists the supported modern Authentication Methods, as available with Conditional Access policies. Fourth column lists the legacy Authentication Methods used with Per-User MFA, and finally the last column lists the legacy Self Service Password Reset Authentication Methods.
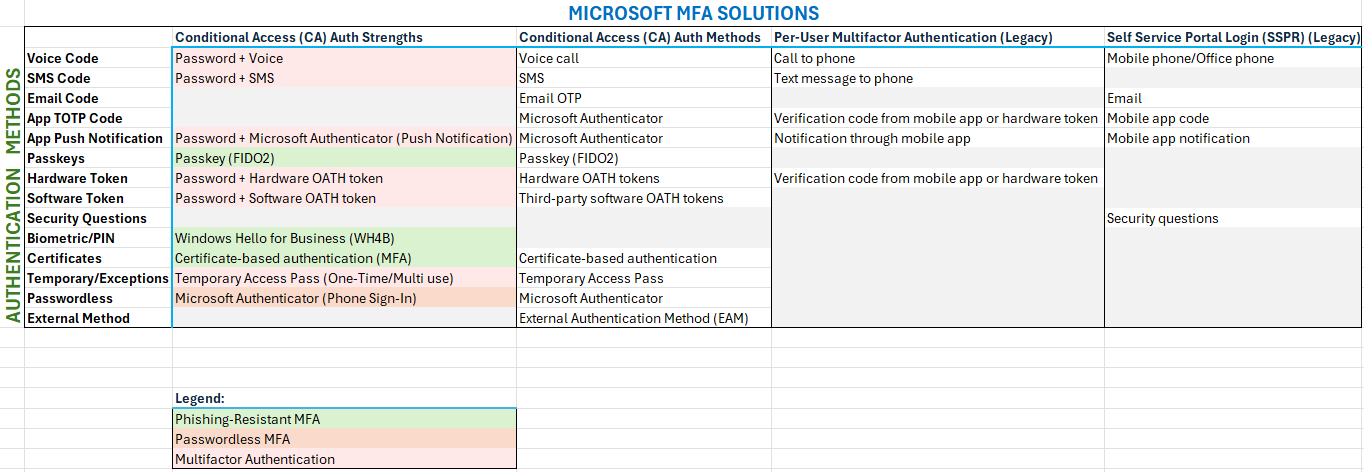
Legacy MFA and SSPR Policies
- Managed separately:
- Per‑user MFA policy (for multifactor authentication)
- SSPR (Self‑Service Password Reset) policy (for password resets)
These policies cannot be scoped granularly—they apply tenant-wide with no group-level targeting.
- Planned deprecation: as mentioned previously, these policies will be deprecated by Microsoft at the end of September, 2025.
Modern Authentication Methods Policies
- Unified management: A consolidated, granular policy that covers both MFA and SSPR methods. Admins can target all users, specific groups, or exclude groups enabling much finer control.
- Supports modern, secure authentication methods:
- Passkey (FIDO2)
- Hardware OATH token
- Windows Hello for Business
- Certificate-based authentication (CBA)
- Microsoft Authenticator
- TOTP code
- Push
- Passwordless
- Temporary Access Pass (TAP)
- QR code
- External Authentication Method (EAM)
- SMS (text message)
- Voice call
- Legacy methods like SMS and voice are still supported and include advanced options with more configuration flexibility.
- Integration with Conditional Access:
- Modern authentication methods integrate with Conditional Access policies to enforce MFA on certain conditions, such as every login to an application, or logins from external sources, etc.
- Integration with Authentication Strengths:
- Authentication Strengths: can be defined as built-in policies such as “Phishing‑resistant MFA” (only FIDO2, Windows Hello, or certificate-based), “Passwordless MFA strength”, etc., to enforce higher security based on scenario.
- Improved configuration: Capabilities like customizing call greetings, filtering which phone types are valid, showing app sign-in location, and more – none are available in legacy experience.
Migration Overview: Legacy to Modern Policy
It is recommended to perform the Automatic Migration to streamline the migration process. Below, you will find step by step guides for both Automatic and Manual migration options.
Some tenants, especially newer ones, may already be auto-provisioned in a post-migration state, without rollback options. Most tenants, however, will display Migration Status: Not Started and need to go through the migration process.
Automatic Migration
- Login to Microsoft Entra admin center
- Open the Authentication Methods > Policies section
- Click on Begin automated guide to use the migration wizard:
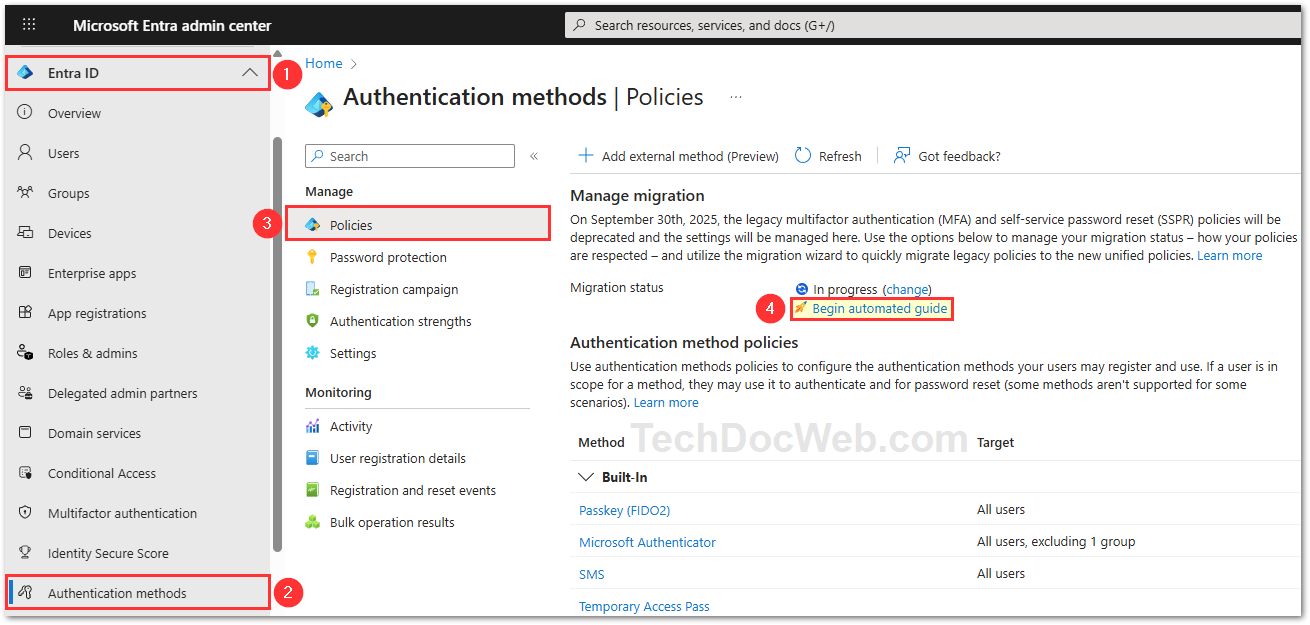
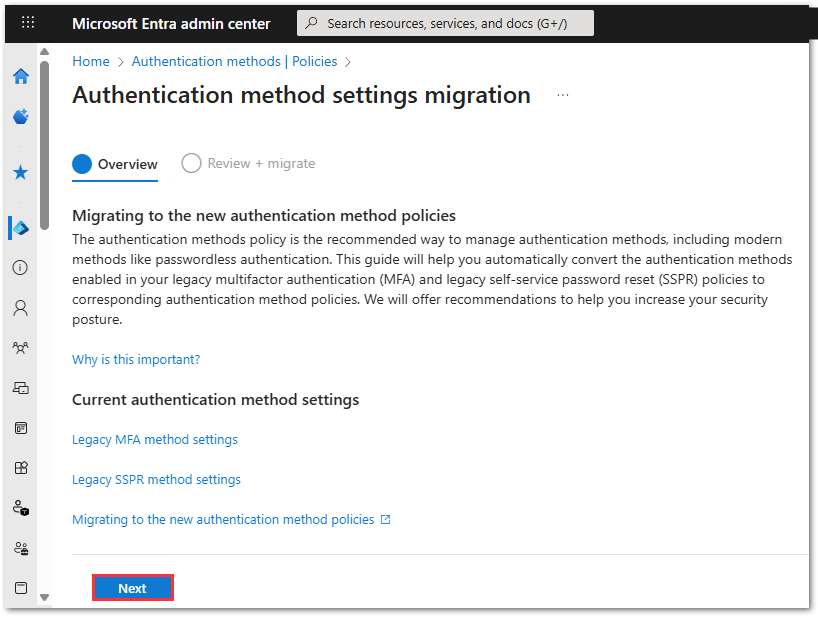
- Review the current authentication method settings and click Next. The wizard audits legacy configurations and mirrors them into the new policy. You can customize options before finalizing.
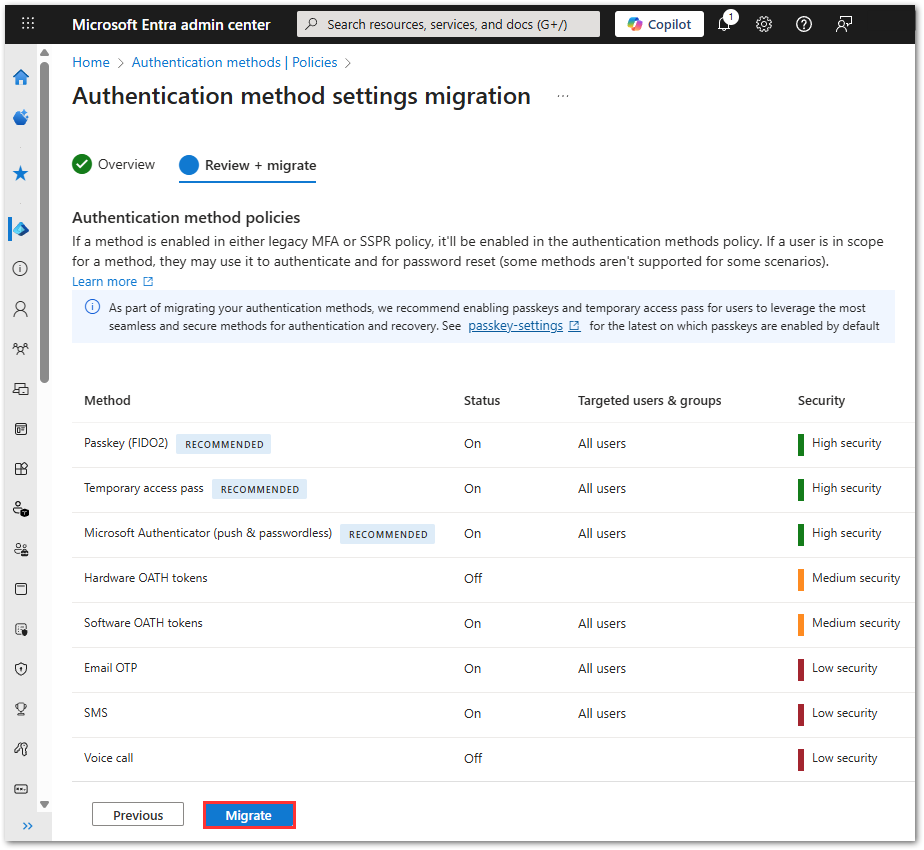
- Review the migration method settings, ensuring all relevant methods and targeted groups are accurate. Click Migrate to initiate the migration process.
- Click Continue to complete the migration process.
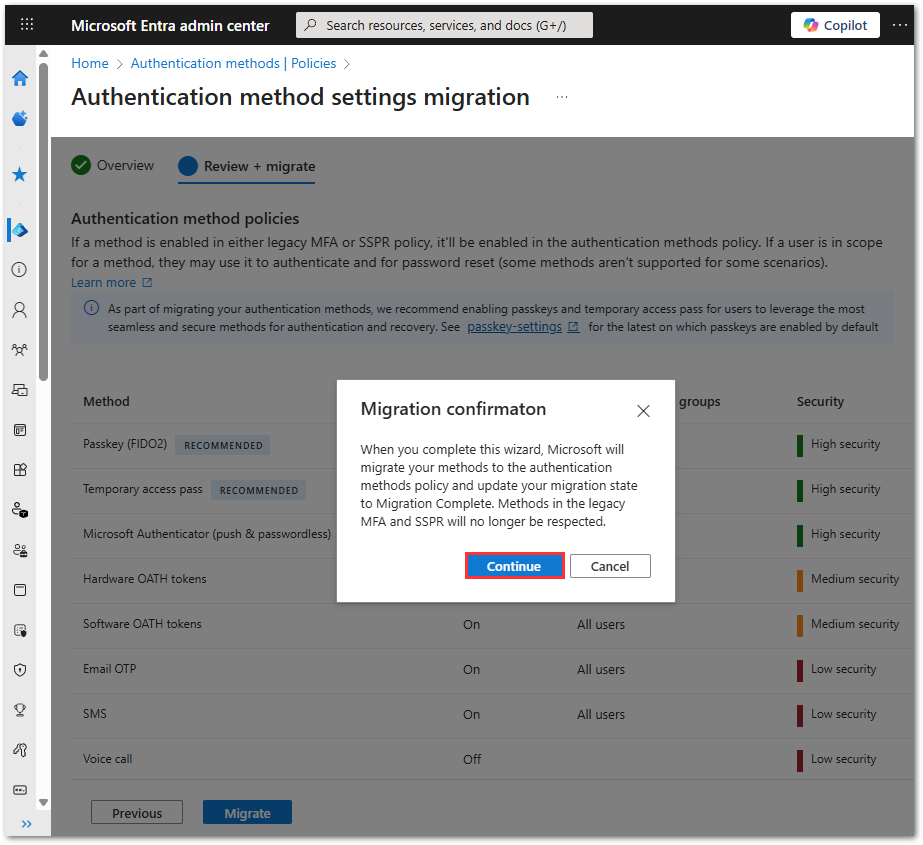
- You’ll be taken to the updated Authentication Methods screen. Migration is complete.
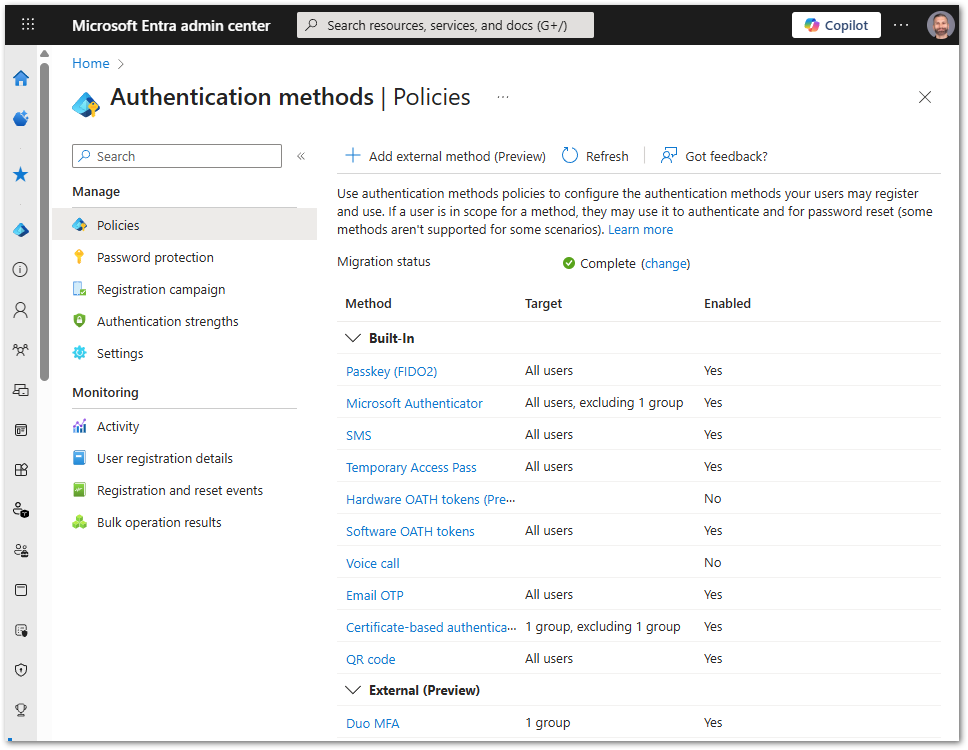
- Test authentication for MFA and SSPR to ensure successful operation.
Manual Migration
- Go to the Microsoft Entra admin center
- Open the Authentication Methods > Policies section
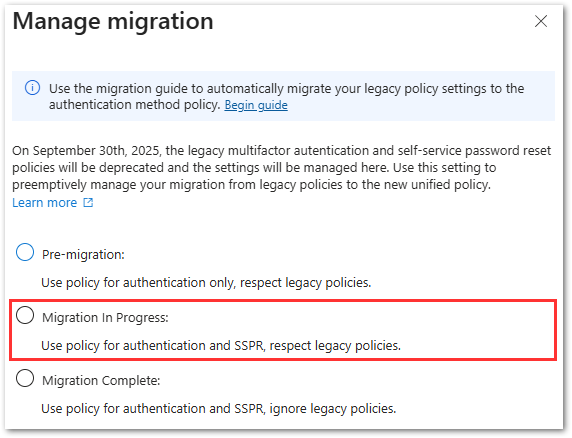
- Next to the Migration Status, click on Change and set the migration status to Migration In Progress.
Explanation of statuses:- Pre-migration: Only modern policy applies to sign-in; legacy still active.
- Migration in Progress: Both modern and legacy policies apply.
- Migration Complete: Only modern policy governs—legacy is ignored (except SSPR security questions, which still remain).
- Enable Passkey (FIDO2) and Microsoft Authenticator authentication methods under the new methods policy for All Users. At least one method needs to be enabled for all users in the tenant in order for the migration to be successful. In our case we are selecting two methods.
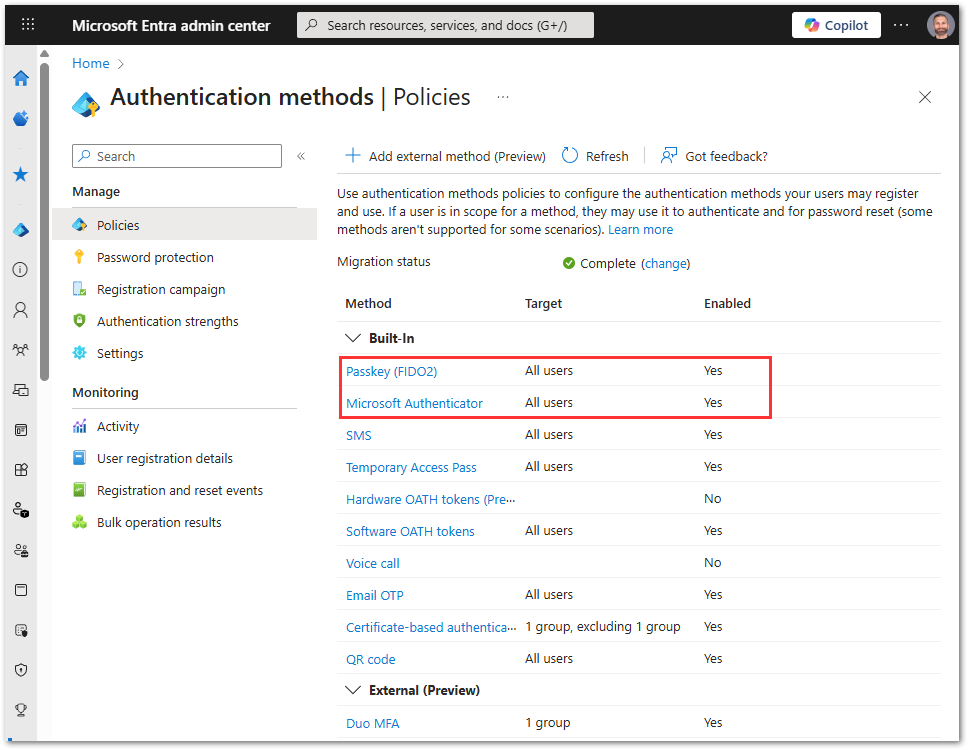
- Audit current legacy policies:
- Check which legacy authentication methods are enabled, so you know how to approach the authentication methods in the modern policy.
Ensure that whichever legacy authentication methods you have enabled now, match within the modern authentication methods.
Review the below areas:- Per-User Multifactor Authentication – Service Settings tab, under Verification Options
- Self Service Password Reset (SSPR) – listed as Password Reset in Entra and Azure portals. With SSPR, all methods except for the Security Questions are available with modern Authentication Methods policies. However, Email is not available as part of the new Authentication Strengths.
- Check which legacy authentication methods are enabled, so you know how to approach the authentication methods in the modern policy.
- Remove legacy Per-User MFA authentication methods
- Navigate to Identity > Users > All Users and click on Per-User MFA and uncheck all options.
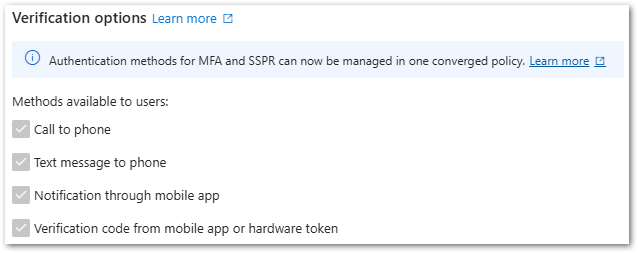
- Navigate to Identity > Users > All Users and click on Per-User MFA and uncheck all options.
- Remove legacy SSPR authentication methods
- Navigate to Protection > Password Reset > Authentication Methods > Methods Available to Users and uncheck all options
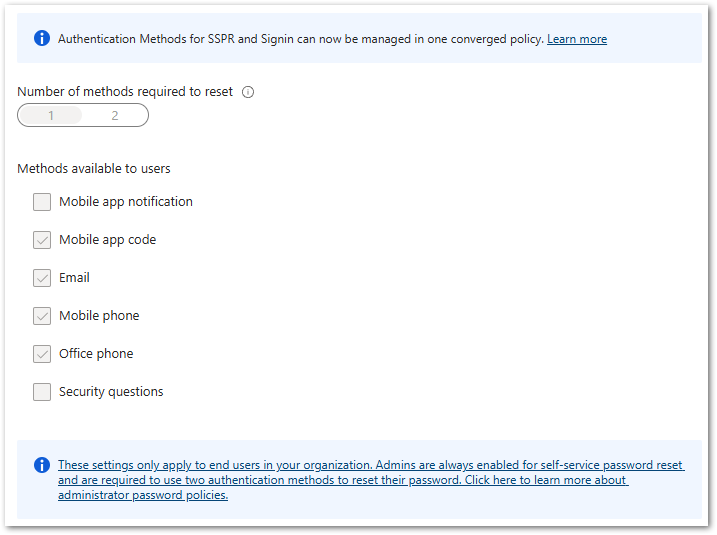
- Navigate to Protection > Password Reset > Authentication Methods > Methods Available to Users and uncheck all options
- Finalize migration:
- Test authentication for MFA and SSPR to ensure successful operation.
- After testing, set status to Migration Complete to disable legacy controls permanently. You can roll back to “In Progress” if needed during transition.
- Microsoft clarifies there should be no disruption to user authentication during this migration process if you follow the steps.
- Migration order matters: The system checks the modern Authentication Methods first, then falls back to legacy only if a method isn’t enabled.
- Post-migration cleanup:
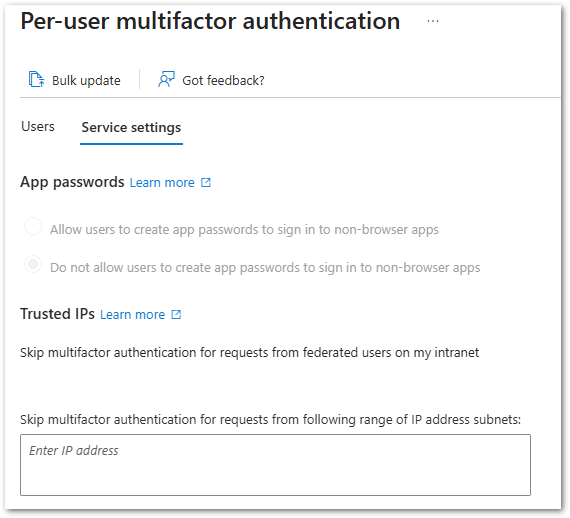
- Remove or disable legacy settings like “remember MFA,” trusted IPs, and per-user enforcement these are outdated and pose security risks.
- It’s also highly advisable to disable the App Passwords, as this is an older approach of authentication for legacy clients and bypasses the MFA.
Found this useful? Share with others: